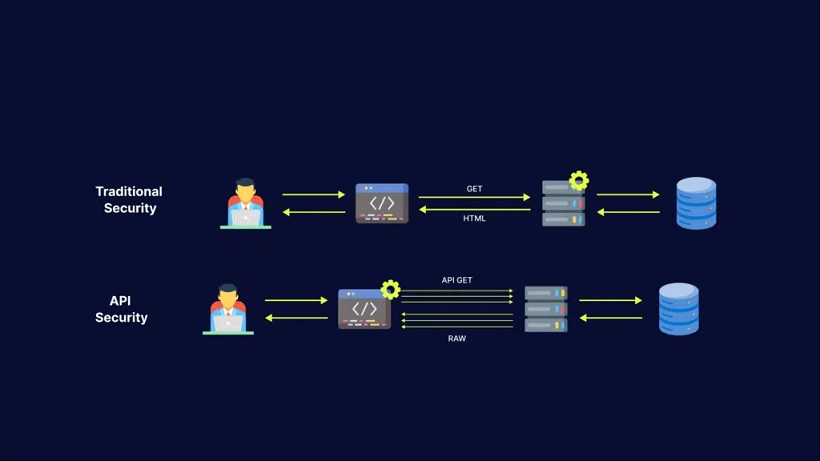
In the ever-evolving landscape of web development and data security, understanding the nuances of proxy detection has become paramount for developers seeking to enhance their applications’ integrity and performance. As online threats grow more sophisticated, the ability to differentiate between legitimate users and masked identities via proxy servers is crucial. This comprehensive guide delves into the realm of Proxy Detection API documentation, offering developers a detailed roadmap to effectively implement these tools within their projects. Whether you are working on e-commerce platforms, content delivery networks, or security applications, leveraging a robust proxy detection API can significantly bolster your system’s defenses against fraudulent activities and abuse. In this guide, we will explore the essential components of various proxy detection APIs, providing insights into their functionalities, implementation strategies, and best practices. From understanding the underlying technologies to navigating the intricacies of API documentation, this article aims to equip developers with the knowledge necessary to seamlessly integrate proxy detection capabilities into their applications. Whether you are a seasoned developer or new to the field, this guide will serve as an invaluable resource in your quest to safeguard your digital environments against proxy-related threats.
– Understanding Proxy Detection API Documentation Essentials
Effective utilization of a proxy detection API relies heavily on a thorough understanding of the proxy detection API docs. These documentation resources provide crucial information regarding endpoint configurations, request and response formats, and authentication mechanisms, all of which are essential for seamless integration into applications. Developers must familiarize themselves with the specific parameters and options available, as this knowledge enables them to accurately implement the API in varied scenarios, ensuring reliable detection of proxy usage.
Moreover, the proxy detection API docs typically contain use case examples and best practices that can significantly enhance implementation strategies. By examining these cases, developers can better grasp how to handle specific situations, such as distinguishing between residential and datacenter proxies or identifying potential fraudulent activity. Comprehensive documentation not only empowers developers to leverage the full capabilities of the proxy detection API but also minimizes the risk of errors that could compromise application performance and security.
– Key Features of Proxy Detection APIs
One of the primary features of a robust proxy detection API is its ability to provide real-time analysis and verification of IP addresses. This functionality allows developers to quickly determine whether a given IP is associated with a known proxy service, enabling immediate responses to potential security threats. Additionally, advanced APIs often incorporate machine learning algorithms that improve detection accuracy over time, adapting to new proxy patterns and enhancing the overall reliability of the service.
Another significant aspect is the granularity of data offered by these APIs, which typically includes details about the type of proxy (e.g., residential, datacenter, or mobile), geolocation information, and risk scoring. This level of detail assists businesses in making informed decisions regarding user engagement and fraud prevention. Furthermore, the best proxy detection APIs provide comprehensive analytics and reporting capabilities, allowing organizations to monitor trends and patterns in proxy usage, thus facilitating proactive measures against malicious activities.
– Best Practices for Implementing Proxy Detection
When implementing a proxy detection system, developers should prioritize the integration of a multi-faceted approach that leverages various techniques for comprehensive coverage. Utilizing a combination of IP address verification, behavioral analysis, and device fingerprinting can significantly enhance detection accuracy. It is crucial to regularly update the proxy detection API docs to reflect the latest trends and patterns in proxy usage, as this helps in maintaining the effectiveness of the solution against evolving threats. Additionally, employing a scoring mechanism for risk assessment allows businesses to customize their responses based on the level of potential threat posed by detected proxies.
Furthermore, ensuring that the proxy detection API is seamlessly integrated into existing workflows is vital for operational efficiency. Implementing proactive monitoring and alert systems will enable organizations to respond promptly to suspicious activities, reducing the risk of data breaches and fraud. Thorough testing and validation of the detection processes are also essential to ensure reliability and minimize false positives, which can hinder legitimate user experiences. By adhering to these best practices, businesses can effectively utilize proxy detection APIs to safeguard their digital environments and enhance their security posture.
In conclusion, understanding the intricacies of proxy detection APIs is essential for developers aiming to enhance the security and integrity of their applications. By leveraging the insights provided in this guide, developers can effectively implement these tools to identify and mitigate risks associated with proxy usage. As the digital landscape continues to evolve, staying informed about the latest advancements in proxy detection technology will empower developers to create more resilient systems. Ultimately, a robust approach to proxy detection not only safeguards user data but also fosters trust and reliability in the applications we build.